$1M Intercepted from the Balancer Hack
Nov 11, 2025 | Bitfinding Team
On Monday, November 3rd, 2025, Bitfinding's Exploit Interception Agent deployed countermeasures in less than 12 seconds, detecting and intercepting part of the exploits targeting Balancer's V2 pools on the Ethereum chain. Our whitehat bot successfully secured over $975,000 in assets, preventing further losses in one of the year's most sophisticated DeFi attacks. Notably, our initial intervention landed in the very next block after the attacker's first exploit, highlighting the lightning-fast response of our system.
The Attack Unfolds
The Balancer exploit originated from a subtle rounding error in the protocol's upscale function during EXACT_OUT swaps within Composable Stable Pools, allowing attackers to drain tokens like WETH, osETH, and wstETH from pools on Ethereum, Arbitrum, Base, and other networks.
For a detailed technical breakdown, see the explanations from Unvariant and Coinspect.
According to Balancer's preliminary postmortem, the incident affected Composable Stable Pools across multiple networks, with immediate responses including pausing pools, freezing assets, and whitehat recoveries reducing the net impact. The root cause involved deferred settlement in batch swaps allowing extreme low-liquidity states, combined with the rounding flaw. Final losses were estimated around $98 million after mitigations, though initial exploits exceeded $128 million.
The vulnerability, undetected despite multiple audits, enabled attackers to artificially suppress pool token (BPT) values and arbitrage the discrepancies.
Timeline
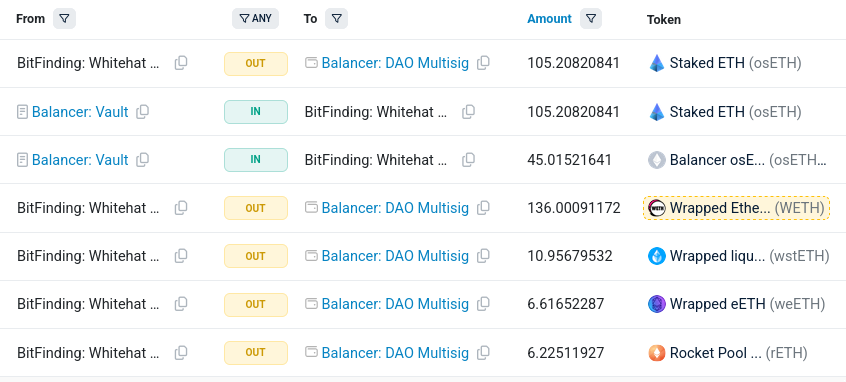
2025-11-03 07:46:47 - Attacker executes initial exploit. Tokens Lost: 6,587.44 WETH , 6,851.12 osETH and 4,259.84 wstETH.
2025-11-03 07:46:59 - 12 seconds later, Bitfinding's Agent identifies, reconstructs the attack. Tokens Recovered: 135.856 WETH, 10.956 wstETH and 105.21 osETH.
2025-11-03 08:33:47 - Further interceptions. Tokens Recovered: 6.225 rETH, and 6.616 weETH.
2025-11-03 11:19:00 - Informed SEAL about the exploit, discussed with pcaversaccio, and got in touch with the Balancer team.
2025-11-04 02:32:00 - Send all the recovered funds to the Balancer DAO
2025-11-07 13:36:00 - Balancer team informed us about additional stuck funds in the contract.
2025-11-08 20:04:35 - The remaining osETH are extracted and also sent to the Balancer DAO.
A special shoutout to @pcaversaccio for always being helpful and to the Balancer team (Danko, Fabio, Juani, and Daniel) for their collaboration throughout the return process.
Conclusion
We're grateful to have helped return funds to a core DeFi protocol. Our interception agent runs as a public good: it watches the chain in real time, models likely exploits, and when a pattern is confirmed it rebuilds the attacker's path and tries to land a preemptive whitehat transaction first to move assets to safety. In this case it acted one block after the first exploit and secured about $1M.
Unblind applies the same concept to user signatures, protecting them from drainers, scams and mistakes. It explains transactions in plain language, flags unexpected behavior, and empowers users and platforms with the knowledge required to operate in hostile blockchain environments. If you run a wallet, custody platform, or DAO treasury and want this by default, Unblind easily integrates via API. Please get in touch below.